Bypass the CertPathValidatorException caused by malformed OCSP response
hackAfter the Java update(Version 8 Update 31), the Juniper VPN applet stopped
working due to the java.security.cert.CertPathValidatorException:
security: Failing over to CRLs: java.security.cert.CertPathValidatorException: OCSP response does not include a response for a certificate supplied in the OCSP request
javax.net.ssl.SSLHandshakeException: java.security.cert.CertificateException: java.security.cert.CertPathValidatorException: OCSP response does not include a response for a certificate supplied in the OCSP request
at sun.security.ssl.Alerts.getSSLException(Alerts.java:192)
at sun.security.ssl.SSLSocketImpl.fatal(SSLSocketImpl.java:1937)
at sun.security.ssl.Handshaker.fatalSE(Handshaker.java:302)
at sun.security.ssl.Handshaker.fatalSE(Handshaker.java:296)
... ...It looks like the SSL authentication handshake goes extra miles to obtain the revocation status of the digital certificate via OCSP protocol. The log also shows that our certificate provider, digicert doesn’t honor the OCSP request:
network: Connecting http://ocsp.digicert.com/ with proxy=DIRECT
network: Connecting http://ocsp.digicert.com:80/ with proxy=DIRECT
security: Failing over to CRLs: java.security.cert.CertPathValidatorException: OCSP response does not include a response for a certificate supplied in the OCSP requestThe workaround is pretty simple, just disable OCSP in Advanced tab of Java Control Panel:
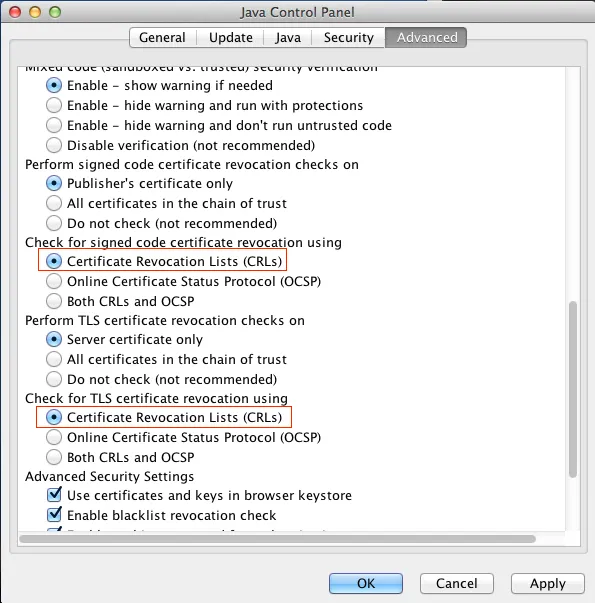
Restart your browser to apply the option, you should be good to go.