Define the (G, E, D):
G: randomize algorithm to generate key pairs (pk, sk).
E(pk, m) takes m ∈ M m\in M m ∈ M c ∈ C c\in C c ∈ C
D(sk, c) takes c ∈ C c \in C c ∈ C m ∈ M m \in M m ∈ M ⊥ \perp ⊥
Define Trapdoor function(TDF)
G: randomize algorithm to generate key pairs (pk, sk).
F ( p k , ⋅ ) F(pk, \cdot) F ( p k , ⋅ ) X → Y X \to Y X → Y F − 1 ( p k , ⋅ ) F^{-1}(pk, \cdot) F − 1 ( p k , ⋅ ) Y → X Y \to X Y → X F ( p k , ⋅ ) F(pk, \cdot) F ( p k , ⋅ )
TDF is secure if F ( p k , ⋅ ) F(pk, \cdot) F ( p k , ⋅ )
Construct
Use secure TDF, symmetric auth encryption defined over (K, M, C) and hash function H → K H \to K H → K random oracle ):
E(pk, m):
x ← X x \leftarrow X x ← X y ← F ( p k , x ) y \leftarrow F(pk, x) y ← F ( p k , x ) k ← H ( x ) k \leftarrow H(x) k ← H ( x ) c ← E ( k , m ) c \leftarrow E(k, m) c ← E ( k , m ) output (y, c)
D(sk, (y, c))
x ← F − 1 ( s k , y ) x \leftarrow F^{-1}(sk, y) x ← F − 1 ( s k , y ) k ← H ( x ) k \leftarrow H(x) k ← H ( x ) m ← D ( k , c ) m \leftarrow D(k, c) m ← D ( k , c ) output m
Never use TDF to encrypt the message directly!
RSA Trapdoor permutation
G G G p , q ≈ 1024 b i t s p, q \approx 1024 bits p , q ≈ 1024 bi t s N = p ⋅ q N = p \cdot q N = p ⋅ q e , d e, d e , d e ⋅ d = 1 ( m o d ϕ ( N ) ) e \cdot d = 1 (mod \ \phi(N)) e ⋅ d = 1 ( m o d ϕ ( N )) p k = ( N , e ) pk = (N, e) p k = ( N , e ) s k = ( N , d ) sk = (N, d) s k = ( N , d )
F ( p k , x ) : R S A ( x ) = x e ∈ Z n F(pk, x): RSA(x) = x^e \in Z_n F ( p k , x ) : RS A ( x ) = x e ∈ Z n F − 1 ( s k , y ) = y d = R S A ( x ) d = x e d = x k ϕ ( N ) + 1 = ( x ϕ ( N ) ) k ⋅ x = x F^{-1}(sk, y) = y^d = RSA(x)^d = x^{ed} = x^{k\phi(N) + 1} = (x^{\phi(N)})^k \cdot x = x F − 1 ( s k , y ) = y d = RS A ( x ) d = x e d = x k ϕ ( N ) + 1 = ( x ϕ ( N ) ) k ⋅ x = x
E, D: symmetric encryption. H: Z N → K Z_N \to K Z N → K
E ( p k , m ) E(pk, m) E ( p k , m )
choose random x in Z N Z_N Z N
y ← R S A ( x ) = x e , k ← H ( x ) y \leftarrow RSA(x) = x^e, k \leftarrow H(x) y ← RS A ( x ) = x e , k ← H ( x ) output (y, E(k, m))
D ( s k , ( y , c ) ) D(sk, (y, c)) D ( s k , ( y , c )) D ( H ( R S A − 1 ( y ) ) , c ) → m D(H(RSA^{-1}(y)), c) \to m D ( H ( RS A − 1 ( y )) , c ) → m
If we use RSA directly to exchange the session key, k k k c = R S A ( k ) c = RSA(k) c = RS A ( k )
Assume k = k 1 , ⋅ k 2 k = k_1, \cdot k_2 k = k 1 , ⋅ k 2 c = k 1 e ⋅ k 2 e → c / k 1 e = k 2 e c = k_1^e \cdot k_2^e \to c/k_1^e = k_2^e c = k 1 e ⋅ k 2 e → c / k 1 e = k 2 e k 1 , k 2 < 2 3 4 k_1, k_2 < 2^34 k 1 , k 2 < 2 3 4 k 1 , k 2 k_1, k_2 k 1 , k 2 2 34 2^{34} 2 34
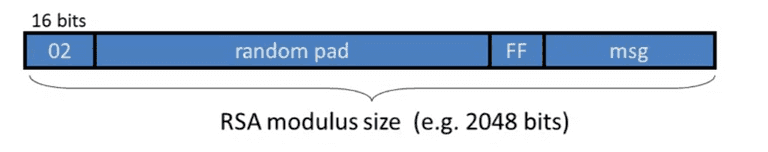
PKCS1
The PKCS1 v1.5 mode 2, used in HTTPS:
PKCS1
The random pad does not contain FF.
Bleichenbacher 1998 attack:
choose r ∈ Z N r \in Z_N r ∈ Z N c ′ ← r e ⋅ c = ( r ⋅ P K C S 1 ( m ) ) e c\prime \leftarrow r^e \cdot c = (r \cdot PKCS1(m))^e c ′ ← r e ⋅ c = ( r ⋅ P K CS 1 ( m ) ) e
send c’ to web server.l
The attacker can recover m with many trials.
/
HTTPS Defence(RFC 5246) treats the incorrect formated messages indistinguishable from correctly formatted RSA blocks.
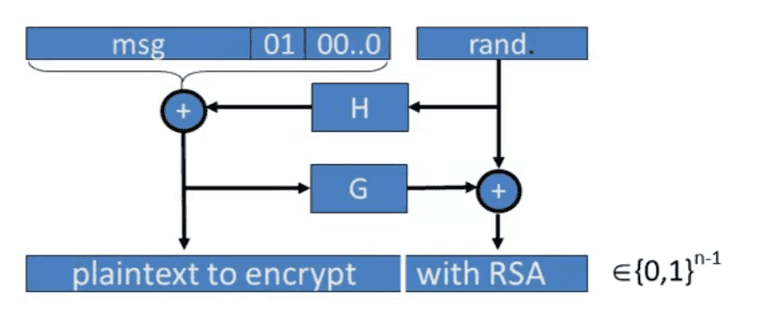
PKCS1 v2.0: OAEP
PKCS
Assume H, and G are random oracles, typically use SHA-256
RSA security analysis
Use d ≈ 2 128 d \approx 2^{128} d ≈ 2 128
Weiner ‘87: if d < N 0.25 d < N^{0.25} d < N 0.25
BD’98: if d < N 0.292 d < N^{0.292} d < N 0.292 0.292 = 1 − 1 2 0.292 = 1 - \frac{1}{\sqrt{2}} 0.292 = 1 − 2 1
Wiener’s attack
e ⋅ d = 1 ( m o d ϕ ( N ) ) → e ⋅ d = k ⋅ ϕ ( N ) + 1 e \cdot d = 1 (\ mod\ \phi(N)) \to e \cdot d = k \cdot \phi(N) + 1 e ⋅ d = 1 ( m o d ϕ ( N )) → e ⋅ d = k ⋅ ϕ ( N ) + 1 ∣ e ϕ ( N ) − k d ∣ = 1 d ⋅ ϕ ( N ) < 1 N |\frac{e}{\phi(N)} - \frac{k}{d}| = \frac{1}{d\cdot \phi(N)} < \frac{1}{\sqrt{N}} ∣ ϕ ( N ) e − d k ∣ = d ⋅ ϕ ( N ) 1 < N 1 ∣ N − ϕ ( N ) ∣ ≤ p + q ≤ 3 N |N -\phi(N)| \le p + q \le 3 \sqrt{N} ∣ N − ϕ ( N ) ∣ ≤ p + q ≤ 3 N
Also:
∣ e N − k d ∣ ≤ ∣ e N − e ϕ ( N ) ∣ + ∣ e ϕ ( N ) − k d ∣ ≤ ∣ e ⋅ 3 N N ϕ ( N ) ∣ + 1 N ≤ 3 N + 1 N ≤ 1 2 d 2 − 1 N + 1 N = 1 2 d 2 \begin{align*}
| \frac{e}{N} - \frac{k}{d} | & \le |\frac{e}{N} - \frac{e}{\phi(N)}| + |\frac{e}{\phi(N)} - \frac{k}{d}| \\
& \le |\frac{e \cdot 3 \sqrt{N}}{N \phi(N)}| + \frac{1}{\sqrt{N}} \\
& \le \frac{3}{\sqrt{N}} + \frac{1}{\sqrt{N}} \\
& \le \frac{1}{2d^2} - \frac{1}{\sqrt{N}} + \frac{1}{\sqrt{N}} \\
& = \frac{1}{2d^2}
\end{align*} ∣ N e − d k ∣ ≤ ∣ N e − ϕ ( N ) e ∣ + ∣ ϕ ( N ) e − d k ∣ ≤ ∣ Nϕ ( N ) e ⋅ 3 N ∣ + N 1 ≤ N 3 + N 1 ≤ 2 d 2 1 − N 1 + N 1 = 2 d 2 1 Fault Attack
When decrypting RSA, we can gain 4x speedup with:
Decrypt mod p x p = c d ∈ Z p x_p = c^d \in Zp x p = c d ∈ Zp
Decrypt mod q x q = c d ∈ Z p x_q = c^d \in Z_p x q = c d ∈ Z p
then combine them to get x = c d ∈ Z N x = c^d \in Z_N x = c d ∈ Z N
Suppose error occurs when computing x q x_q x q x p x_p x p x ′ x\prime x ′ g c d ( ( x ′ ) e − c , N ) = p gcd((x\prime)^e -c, N) = p g c d (( x ′ ) e − c , N ) = p
Bad random generate may get the same p, different q, then g c d ( N 1 , N 2 ) = p gcd(N_1, N_2) = p g c d ( N 1 , N 2 ) = p
ElGamal Public-key System
We can use Diffie-Hellman protocol to build public key. Intuitively:
Use A as public key: A = g a A = g^a A = g a g b g^b g b k = g a b k = g^{ab} k = g ab
Key generator:
choose random geneator g in G, and random a in Z n Z_n Z n
output sk = a, pk = (g, h = g a h=g^a h = g a
H: G 2 → K G^2 \to K G 2 → K
Encryption:
E ( p k = ( g , h ) , m ) E(pk=(g, h), m) E ( p k = ( g , h ) , m )
b ∈ Z N , u ← g b , v ← h b b \in Z_N, u \leftarrow g^b, v \leftarrow h^b b ∈ Z N , u ← g b , v ← h b k ← H ( u , v ) , c ← E ( k , m ) k \leftarrow H(u, v), c \leftarrow E(k, m) k ← H ( u , v ) , c ← E ( k , m ) output (u, c)
Decryption:
v ← u a v \leftarrow u^a v ← u a k ← H ( u , v ) , m ← D ( k , c ) k \leftarrow H(u, v), m \leftarrow D(k, c) k ← H ( u , v ) , m ← D ( k , c ) output m
Encryption is 3x expensive as decryption, while RSA decryption is more expensive.
Twin ElGamal, use ( a 1 , a 2 ) ∈ Z N (a_1, a_2) \in Z_N ( a 1 , a 2 ) ∈ Z N
Review
Review